For the last few projects I have been developing authentication and authorisation systems using ASP .NET Identity and IdentityServer4. The current project being an Azure hosted SaaS, has given me the opportunity to use the Azure Active Directory with .Net 5 hosted as an App Service.
Azure Active Directory
The first thing is to register the application with the active directory. During development I am running the application in two environments, locally as I develop and also hosted in Azure for testing. So I need two app registrations, one local and one for the hosted application:
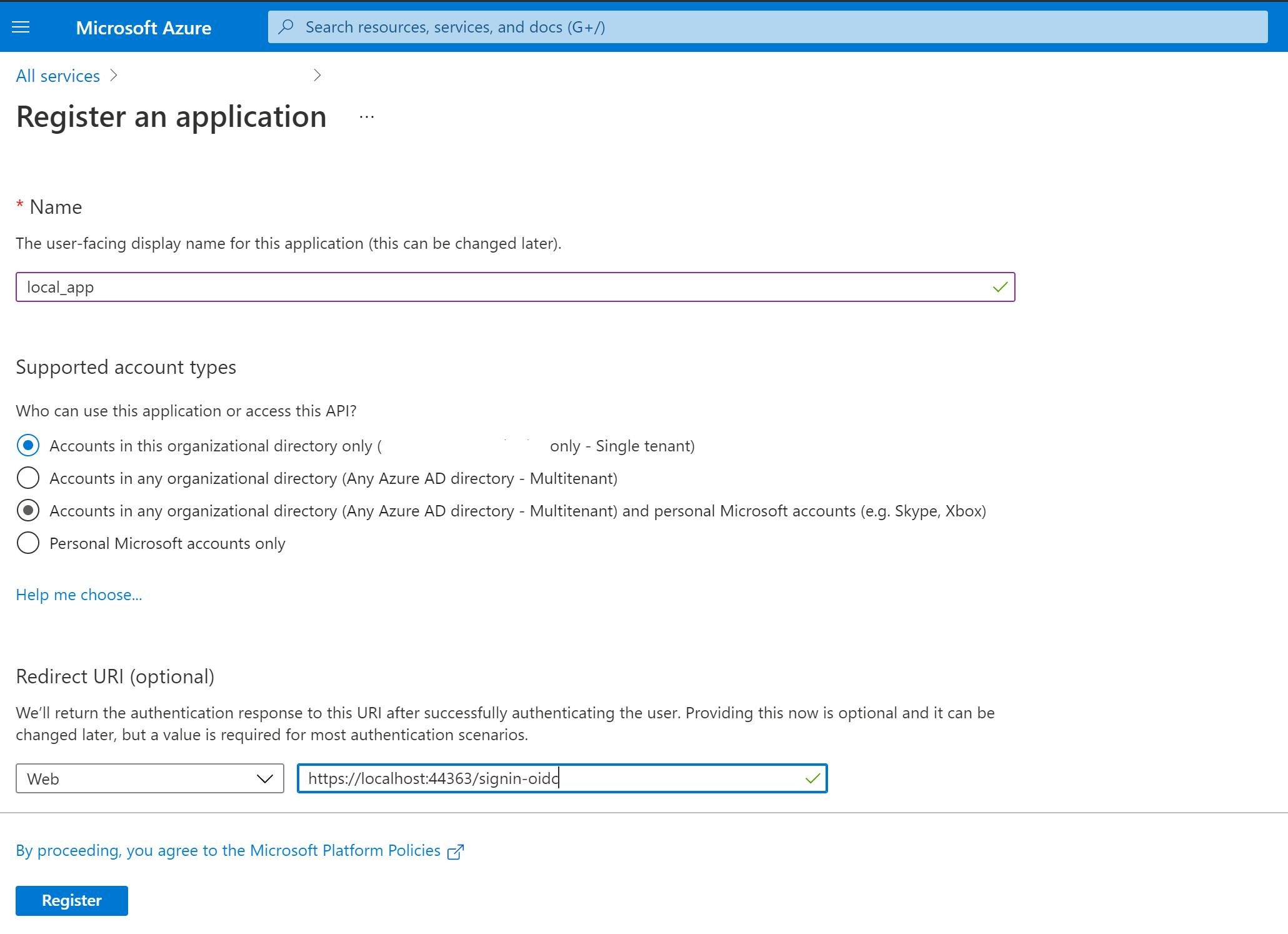
At registration each application is given a unique name. For this application I have a single organisation using a single tenant directory. As the application will be using Microsoft Identity the default application endpoint for OpenIdConnect is used for the Redirect URI:
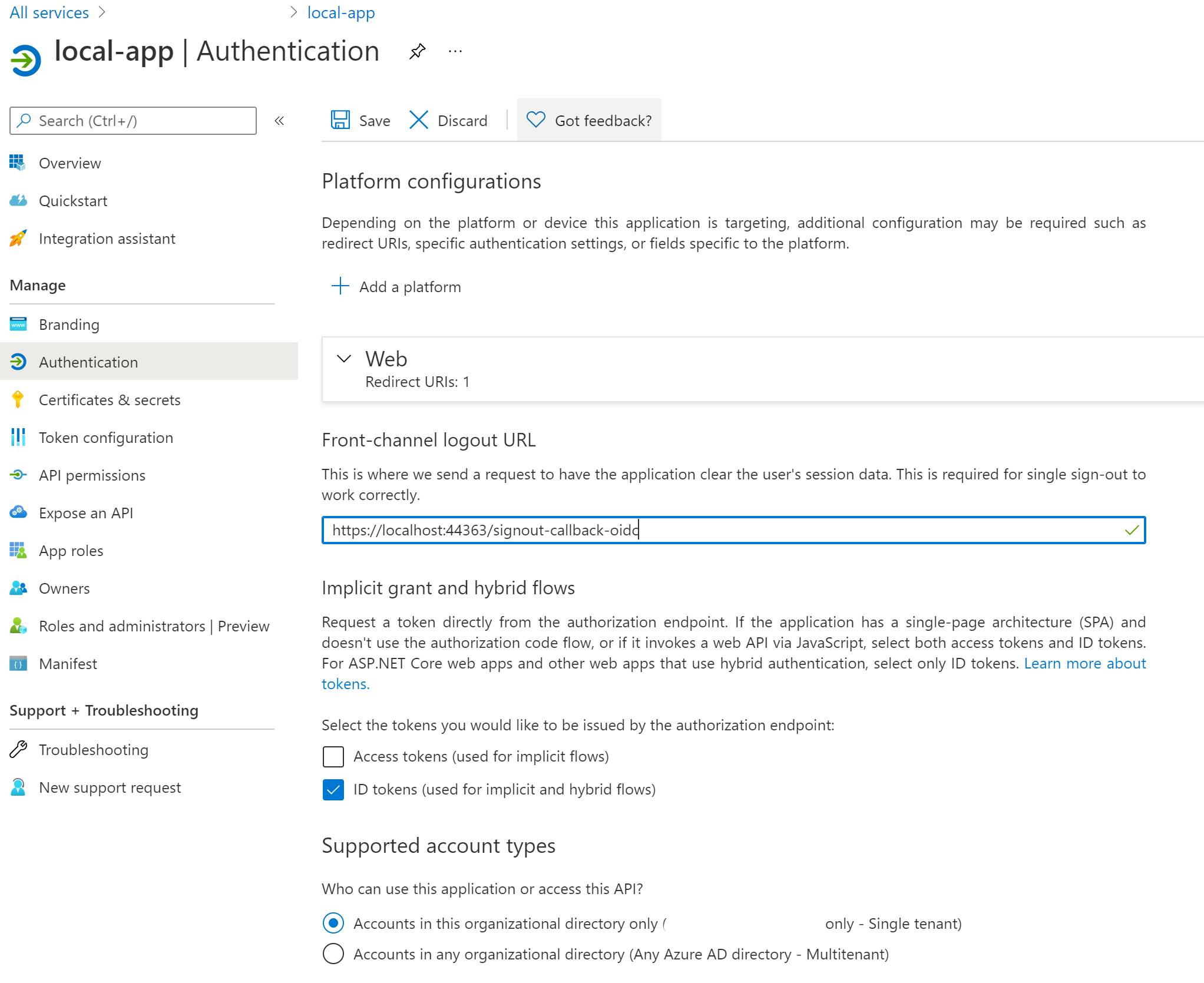
After registering the application you can set the Front-channel logout URL, again I use the OpenIdConnect default. Here I also select the Implicit grant and hybrid flows. As the comment says for ASP .NET Core web apps, select only the ID Tokens:
.Net 5 Authentication
In the application I am using the Microsoft.Identity.Web package:
Firstly, authentication is added in the ConfigureServices(...) method of Startup.cs. The MicrosoftIdentityWebApp(...) options bind to the configuration settings. For the local application these are defined in the appsettings.json file, for the hosted application these will be defined in the Azure App Service Configuration:
public void ConfigureServices(IServiceCollection services)
{
...
// Sign-in users with the Microsoft identity platform
services.AddAuthentication(OpenIdConnectDefaults.AuthenticationScheme)
.AddMicrosoftIdentityWebApp(options => Configuration.Bind("AzureAd", options));
...
}
Then in the Configure(...) method the authentication needs to be used:
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
...
app.UseAuthentication();
...
}
The settings required to hook up to the Azure Active Directory can be found in the Overview of your active directory, primary domain, and of the application registration, client and tenant id's:
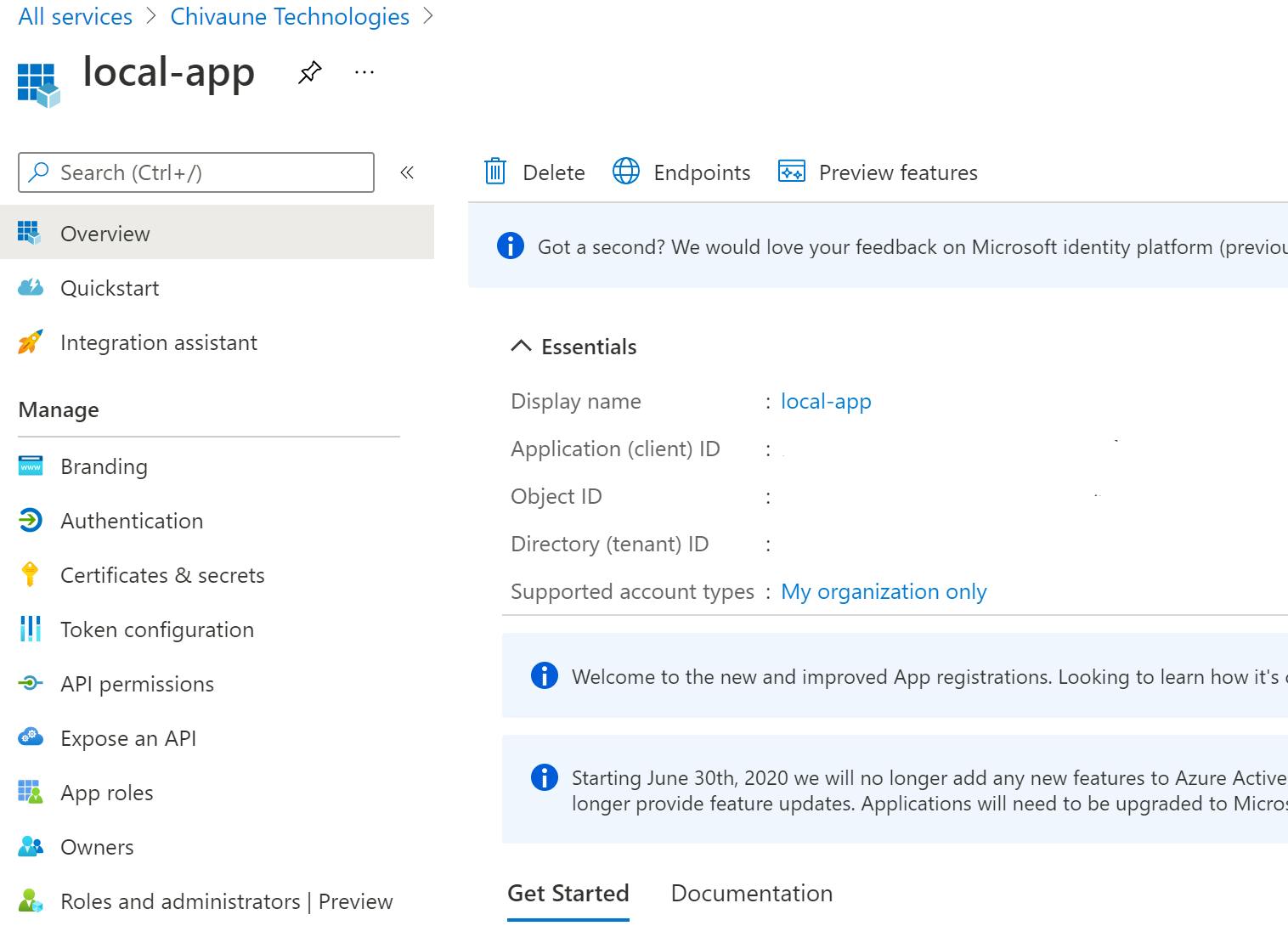
For the local application, settings are stored in the appsettings.json file:
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"CallbackPath": "/signin-oidc",
"SignedOutCallbackPath": "/signout-callback-oidc",
"Domain": "{your Primary domain}",
"ClientId": "{your Application (client) ID}",
"TenantId": "{your Directory (tenant) ID}"
},
Best practice is not to store sensitive information in source code, so the domain, ClientId and TenantId, of the hosted application are stored in the configuration of the Azure App Service.
App Service
The settings are held in the configuration of the App Service:
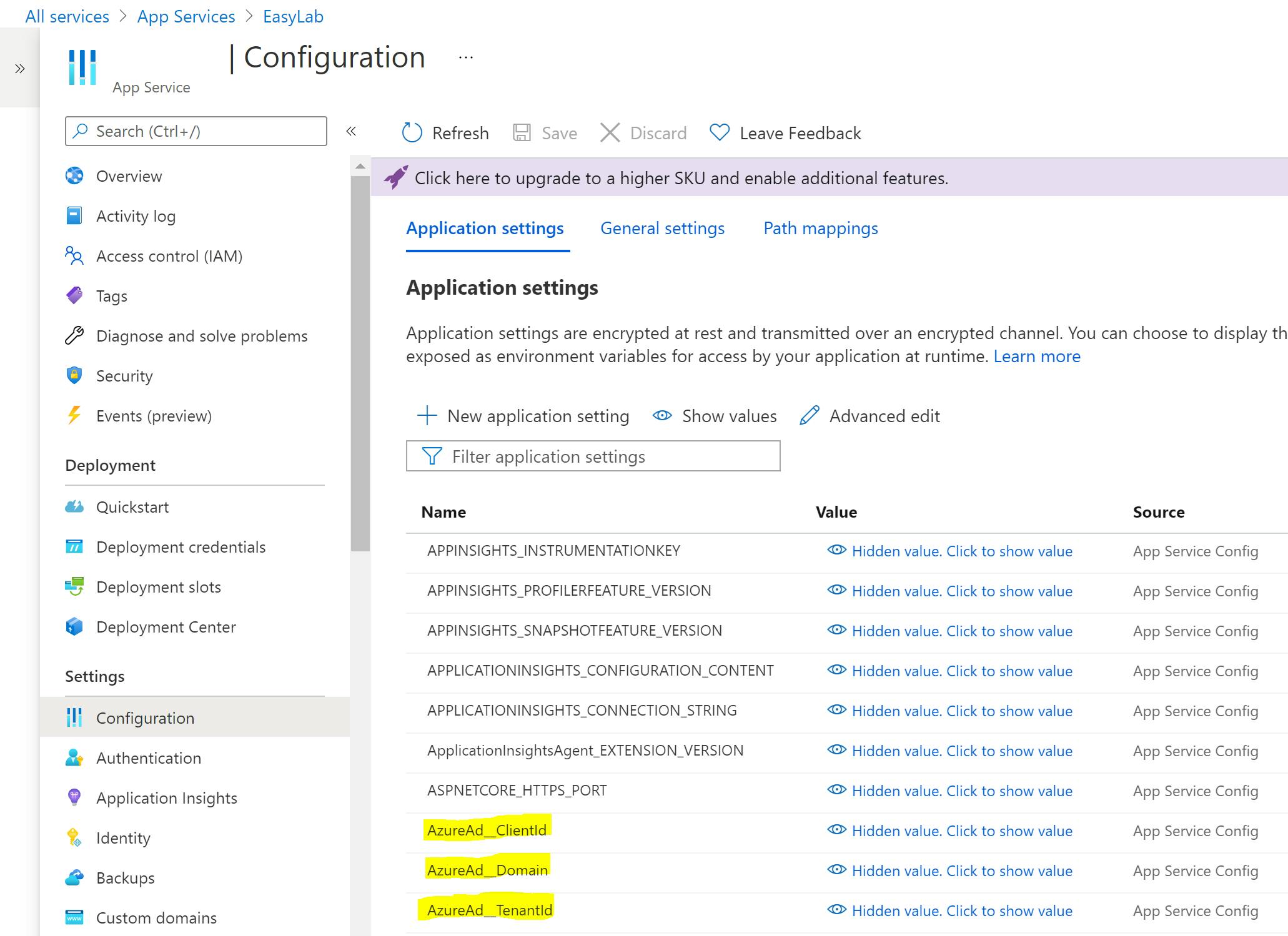
When using an appsettings.json file, values are retrieved using a key composed of the section name, a colon, and the item key eg: AzureAd:Domain. However, when saving the settings to the App Service configuration, two underscores are used instead of he colon eg: AzureAd__Domain.
With everything hooked up correctly the application should prompt you with the Microsoft Pick an account dialog before continuing to you application home page:
When I initially set this up I was recieving a Failed to determine the https port for redirects error. To fix this I needed to add ASPNETCORE_HTTPS_PORT to app service configuration and set it to 443, the default https port.
More information on scaffolding your application to enable you to customise the behaviour can here found here. I hope you find this post useful, I am afraid I can't share the source code at this time as the development is on going.
